
| you can think of this using the analogy of a castle and a moat… The moat and large stone walls is the perimeter security protecting everything inside, with only one way in and one way out. Once you are inside there is very little preventing you from freely moving around, talking to people, touching things, looking at stuff, and so on…. Anyone coming in and out of the front gate can be checked and inspected. And if required, the drawbridge can be raised to prevent to protect the castle.Sounds quite old fashioned right? |
  |
|
The castle and moat methodology is no longer as relevant as it once was due to a variety of reasons…
|
  |
What is Zero Trust and why is it relevant?Zero trust is a security methodology whereby NOBODY AND NOTHING IS TRUSTED.
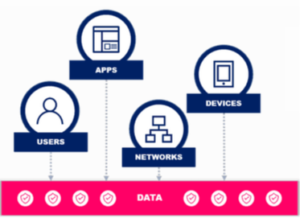
Zero trust is based upon the premise that every actor (User, Application, Service, etc..) is a threat. Typically, there are 4 things that you need to determine if access should be allowed:
Zero trust is not a product or a set of tools/technologies, it is a methodology that requires a set of policies, processes and technology to implement. |
  |
So how do we start on a Zero Trust journey?As we have said Zero Trust is not one thing, there are many aspects. |
  |
|
Here are some good places to start..
|














