Conditional Access templates (Preview)
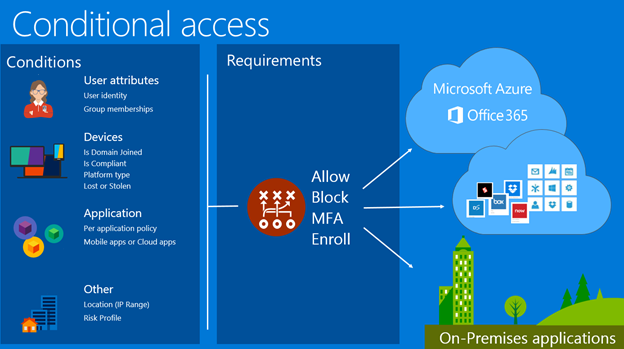
you know you can secure access to your resources using Azure AD Conditional Access policies.
Well, good news, it is now going to be easier to create Conditional Access policies thanks to the use of templates.
To create a Conditional Access policy using templates, connect to your Azure AD portal (https://aad.portal.azure.com/) to access the Azure Active Directory\Security\Conditional Access\Policies blade and use the Create new policy using templates

Conditional Access templates are designed to provide a convenient method to deploy new policies aligned with Microsoft recommendations. These templates are designed to provide maximum protection aligned with commonly used policies across various customer types and locations.
The 14 policy templates are split into policies that would be assigned to user identities or devices. Find the templates in the Azure portal > Azure Active Directory > Security > Conditional Access > Create a new policy from the template.
Important
Conditional Access template policies will exclude only the user creating the policy from the template. If your organization needs to exclude other accounts open the policy and modify the excluded users and groups to include them.
By default, each policy is created in report-only mode, we recommended organizations test and monitor usage, to ensure the intended result, before turning each policy on.
- Identities
- Require multi-factor authentication for admins*
- Securing security info registration
- Block legacy authentication*
- Require multi-factor authentication for all users*
- Require multi-factor authentication for guest access
- Require multi-factor authentication for Azure management*
- Require multi-factor authentication for risky sign-inRequires Azure AD Premium P2
- Require password change for high-risk users requires Azure AD Premium P2
- Devices
- Require compliant or Hybrid Azure AD joined device for admins
- Block access for the unknown or unsupported device platform
- No persistent browser session
- Require approved client apps or app protection
- Require compliant or Hybrid Azure AD joined device or multi-factor authentication for all users
- Use application enforced restrictions for unmanaged devices
* These four policies when configured together, provide similar functionality enabled by security defaults